Introduction to Active Directory and Directory services.
The Active Directory Domain Services role provides a single point of user, desktop, and server administration. To understand Active Directory and its role in a network, you need to know what a directory service is and how it’s used to manage resources and access to resources on a network. Before administrators can use Active Directory to manage users, desktops, and servers in a network, they need an understanding of Active Directory’s structure and its components and objects, which will be covered in this post.
What is AD
Active Directory, a technology from Microsoft to provide network services including LDAP directory services, Kerberos based authentication, DNS naming, secure access to resources, and more. AD uses a single Microsoft Jet database were a variety of services and applications can use to access and store a variety of information. Jet uses a b-tree file structure with transaction logs to ensure recoverability in the event of a system or drive failure. Active Directory is used by system administrators to store information about users, assign security policies, and deploy software. AD is used in many different types and size of environments from the very small (a dozen users) to hundreds of thousands of users in a global environment.
A network directory service, as the name suggests, stores information about a computer network and offers features for retrieving and managing that information. Essentially, it’s a database composed of records or objects describing users and available network resources, such as servers, printers, and applications. Like a database for managing a company’s inventory, a directory service includes functions to search for, add, modify, and delete information. Unlike an inventory database, a directory service can also manage how its stored resources can be used and by whom.
FSMO Roles
Flexible single master operation (FSMO) is an AD feature, where a specialized DC task is used when standard data transfer and update methods are inadequate. Tasks that don’t suit multi master replication are done by flexible single-master operations.
I.e.: – Within Active Directory, objects that are updated on one DC are then replicated to other DC’s through multi-master replication. It is not required for all DC’s to replicate with each other DC as this causes excessive network traffic in large Active Directory deployments. So, DC’s have a complex update pattern that ensures that all servers are updated in a timely fashion without excessive replication traffic. This is better served by Flexible single master operation.
Forest-wide operations master roles: –
Schema master and Domain naming master roles must appear at least once in every forest
- Schema master: – Any update or modification done to the schema must go via the schema master domain controller. For such updates / modification to the schema of a forest, an access must be established with the schema master.
There can be only be one schema master in the entire forest.
E.g.: – While installing Exchange changes are written to Schema.
2. Domain naming master: – The domain controller holding the domain naming master role exclusively controls the addition or removal of domains in the forest.
There can be only one domain naming master in the entire forest.
Any DC running Windows Server 2003 can hold the role of the domain-naming master.
A domain controller running Windows 2000 Server that holds the role of domain naming master must also be enabled as a global catalogue server.
Domain-wide operations master roles: –
- RID master: – It is the task of RID master to allot sequences of relative IDs to each of the DC’s in its domain. When a DC creates a user, group, or computer object, a unique security ID (SID) is assigned to the object.
The SID contains two elements:
One is the domain SID (which is the same name for all SIDs that’s created in a domain)
And the other is an RID, which is unique for each SID created in the domain.
Activities such as moving an object between domains (using Movetree.exe) must be instigated on the domain controller acting as the RID master of the domain (that currently contains the object).
E.g.: “S-1-5-21-3623811015-3361044348-30300820-1013”
Where;
S :- The string is a SID.
1 :- The revision level (the version of the SID specification).
5 :- The identifier authority value.
21-3623811015-3361044348-30300820 :- Domain or local computer identifier
1013 :- A relative id (RID). Any group or user that is not created by default will have a Relative ID of 1000 or greater.
- PDC emulator master: – To ensure consistency, password changes from client computers must be replicated and updated to all domain controllers throughout the domain. The PDC emulator can be configured to synchronize with an external time source. Provides consistency in password experience for users across sites. (To turn off use: AvoidPdcOnWan registry parameter). Double- checks incorrect passwords and reviews new password changes.
The domain controller configured with the PDC emulator role supports two authentication protocols:
The Kerberos V5 protocol
The NTLM protocol
- Infrastructure master: – Tasks such as updating references from objects in its domain to objects in other domains are under the purview of the infrastructure master. The infrastructure master compares its data with that of a global catalogue, which receives regular updates for objects in all domains through replication, thus making the global catalogue data up to date. Say, in a scenario where the infrastructure master suspects outdated data, it fetches updated data from the GC and replicates it to the other domain controllers in a domain.
NB: Unless there is only one domain controller in the domain, the infrastructure master role should not be assigned to the domain controller that is hosting the global catalogue.
If the infrastructure master and global catalogue are on the same domain controller, the infrastructure master will not function.
The infrastructure master will seldom find data that is out of date, so it will never replicate any changes to the other domain controllers in the domain.
In the case where all the domain controllers in a domain are also hosting the global catalogue, all the domain controllers will have the current data and it does not matter which domain controller holds the infrastructure master role.
In scenarios where user / members of a group are renamed / modified, the infrastructure master is responsible for revising the group-to- user references.
When the member of a group is moved or renamed, especially if that member resides in a different domain from the group, the member would temporarily not appear in the group. It is the infrastructure master of the group’s domain’s responsibility to update the group of the new name or location of the member. This prevents the loss of group memberships associated with a user account.
Update is distributed by the infrastructure via multimaster replication.
Structure of AD Database
The structure of AD is as follows (ref image below)
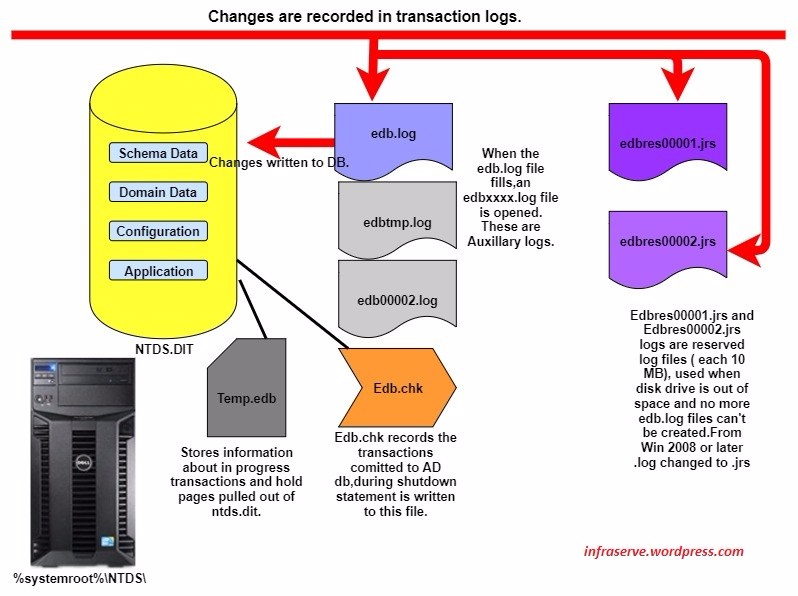
AD Database
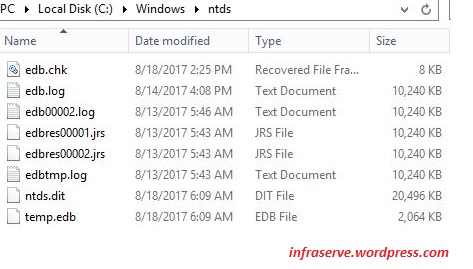
Files in %systemroot%\NTDS\
- Ntds.dit. This is the main ADdatabase. NTDS stands for NT Directory Services. The DIT stands for Directory Information Tree. The Ntds.dit file on a domain controller contains all naming contexts hosted by that domain controller, including the Configuration and Schema naming contexts. A Global Catalogue server stores the partial naming context replicas in the Ntds.dit right along with the full Domain naming context for its domain.
- Edb.log. This is a transaction log. Any changes made to objects in Active Directory are first saved to a transaction log. During low CPU activity, the database engine commits the transactions into the main Ntds.dit database. This ensures that the database can be recovered in the event of a system crash. Entries that have not been committed to Ntds.dit are kept in memory to improve performance. Transaction log files used by the ESE engine (Extensible Storage Engine(ESE), also known as JET Blue, is an ISAM (indexed sequential access method) data storage technology from Microsoft.) are always 10MB.
- Edbxxxxx.log. These are auxiliary transaction logs used to store changes if the main Edb.log file gets full before it can be flushed to Ntds.dit. The xxxxx stands for a sequential number in hex. When the Edb.log file fills up, an Edbtemp.log file is opened. The original Edb.log file is renamed to Edb00001.log, and Edbtemp.log is renamed to Edb.log file, and the process starts over again. ESENT uses circular logging. Excess log files are deleted after they have been committed. You may see more than one Edbxxxxx.log file if a busy domain controller has many updates pending.
- Edb.chk. This is a checkpointfile. It is used by the transaction logging system to mark the point at which updates are transferred from the log files to Ntds.dit. As transactions are committed, the checkpoint moves forward in the Edb.chk file. If the system terminates abnormally, the pointer tells the system how far along a given set of commits had progressed before the termination.
- Edbres1.log and EdbRes2.log. These are reserve log files. If the hard drive fills to capacity just as the system is attempting to create an Edbxxxxx.log file, the space reserved by the Res log files is used. The system then puts an urgent warning on the screen prompting you to act to free up disk space quickly before Active Directory gets corrupted. You should never let a volume containing Active Directory files get even close to being full. File fragmentation is a big performance thief, and fragmentation increases exponentially as free space diminishes. Also, you may run into problems as you run out of drive space with online database defragmentation (compaction). This can cause Active Directory to stop working if the indexes cannot be rebuilt.
- Temp.edb. This is a scratch pad used to store information about in-progress transactions and to hold pages pulled out of Ntds.dit during compaction.
- Schema.ini. This file is used to initialize the Ntds.dit during the initial promotion of a domain controller. It is not used after that has been accomplished.
Next Blogs will be as follows
- AD installation pre-requisites,AD installation procedure
